Smart Policy – smart card integration with active directory
Trouble with smart card logon ? Check our troubleshooting guide here.
Configuring existing smart cards (like CAC, EID, NHS, CPS, …) into a forest is quite complex. Even with specialists, it requires many configuration attempts because the only error messages delivered are “The system could not log you on. Your credentials could not be verified.” or “The smart card certificate used for authentication was not trusted“. Smart Policy has been designed for painless mass integration of existing smart cards.
Operating Systems :
- Windows Vista / Windows 2008 and later to run the Configuration Wizard
- Windows 2000 and later for the UPN mapping method (CAC smart cards)
- Windows Vista / Windows 2008 and later for the Explicit mapping method (EID smart cards)
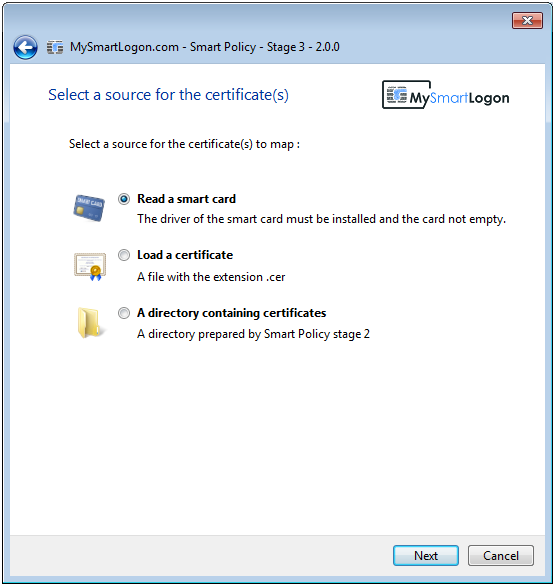
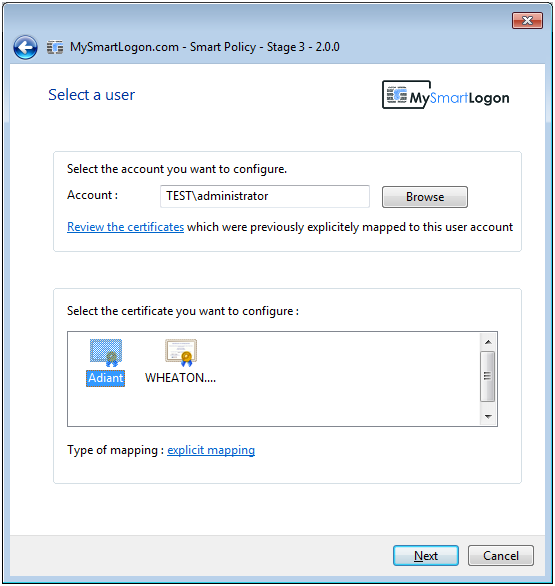
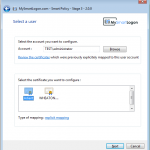
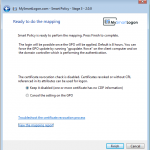
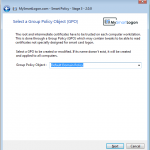
SmartPolicy implements two techniques to map a certificate : UPN mapping (modify the UPN of the account if the certificate includes an UPN) and Explicit Mapping (modify the AltSecurityIdentities attribute of the account to add the subject of the certificate).
Components :
- ctive Directory Certificate Services
This component is required to provide certificates to the domain controller using the template “domain controller authentication”.
Smart Policy has been designed for smart card integration with Active Directory.
As a consequence, there is no additional PKI to manage, no token to purchase and it becomes a nearly free second factor authentication.
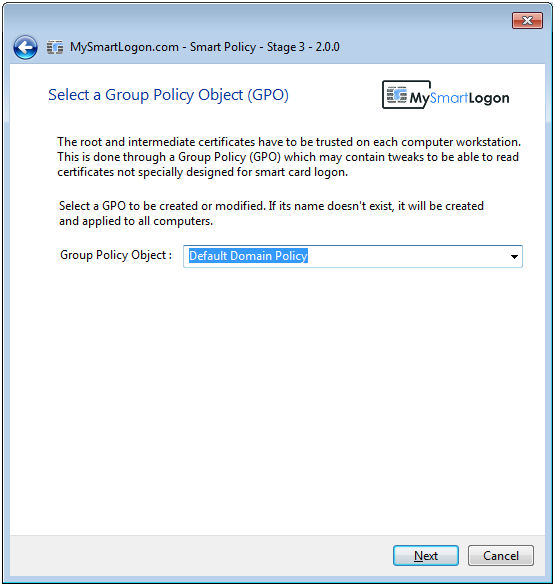
Smart Policy proceeds with a 3 stages process :
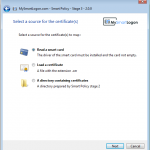
- Acquisition The end user submits its certificate to the system using the web collector or with the program
- Compliance A Security Officer receives the certificate from the previous stage and verify the compliance against a set of security controls (Is it issued by the trusted certificate autorithy ? Does the common name of the certificate match the first name and the last name of the user as indicated in the IAM system ?)
- Configuration An Operator or an integration program like FIM makes the modifications to the Active Directory (account, certificate store) to bind the certificate to the user.