EIDVirtual – Transform an USB Key into a virtual smart card
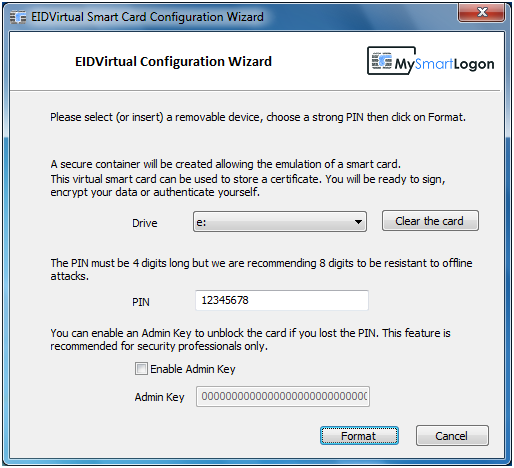
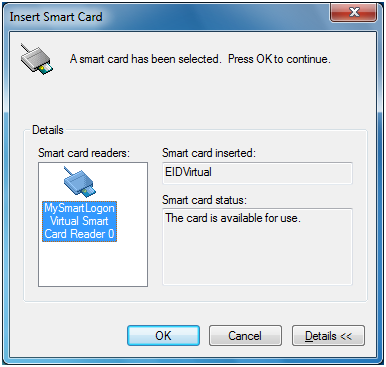
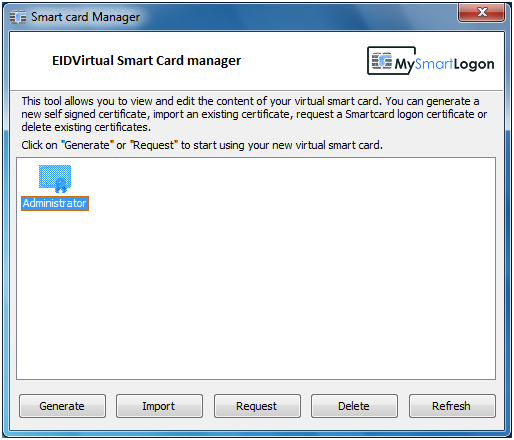
EIDVirtual is a solution to make an USB KEY be recognized as a virtual smart card in the device manager. It can then be used to login with EIDAuthenticate or Active Directory.
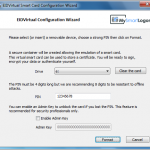
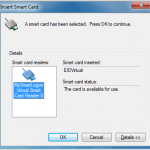
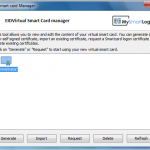
- Windows XP or Windows 2003 or later.
- An USB Key or memory card
This software has been designed for administrators or developers which needs to test processes or some compatibility with smart cards on Windows. The emulation provided is compatible with all smart card scenarios (login on Active Directory or EIDAuthenticate, Radius / VPN / Wifi EAP-TLS authentication, SSL authentication, S/MIME, EFS, Bitlocker, …). As a consequence, it can be used as a fail over mechanism when you need smart cards immediately. The smart card emulation is also compatible with Remote Desktop and recognized by any computer having EIDVirtual installed.
EIDVirtual as been carefully design to protect private keys and the PIN. Private data are encrypted twice : first using an USB Key fingerprint and second using a PIN derivate. Computation are made into the UMDF host process isolated from all other processes.
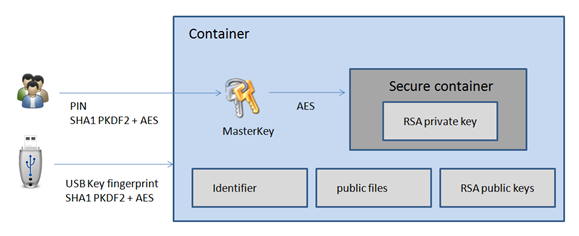
here is NO API to export the private keys.
The token is encrypted using the token fingerprint, including the serial number if available, which can’t be copied. The copy of the token will not be recognized.
The failed authentication attempts are limited to 3, like a real smart card. After one hour, the counter is reseted.
It is the same than the AES provider: RSA Key length – Can be set, 384 bits to 16,384 bits in 8-bit increments.
However, this software solution DO NOT perform hardware protection like :
- Physical isolation from the host CPU
- Physical destruction of the private keys
- Physical PIN enforcement